How to Run Compliance for a Roster
To run compliance from the Roster record:
Navigate to the PowerRoster App > Rosters > Open the Roster that you want to use for the compliance check.
.png)
Select Run Compliance in the Command bar to create a new Compliance Run.
.png)
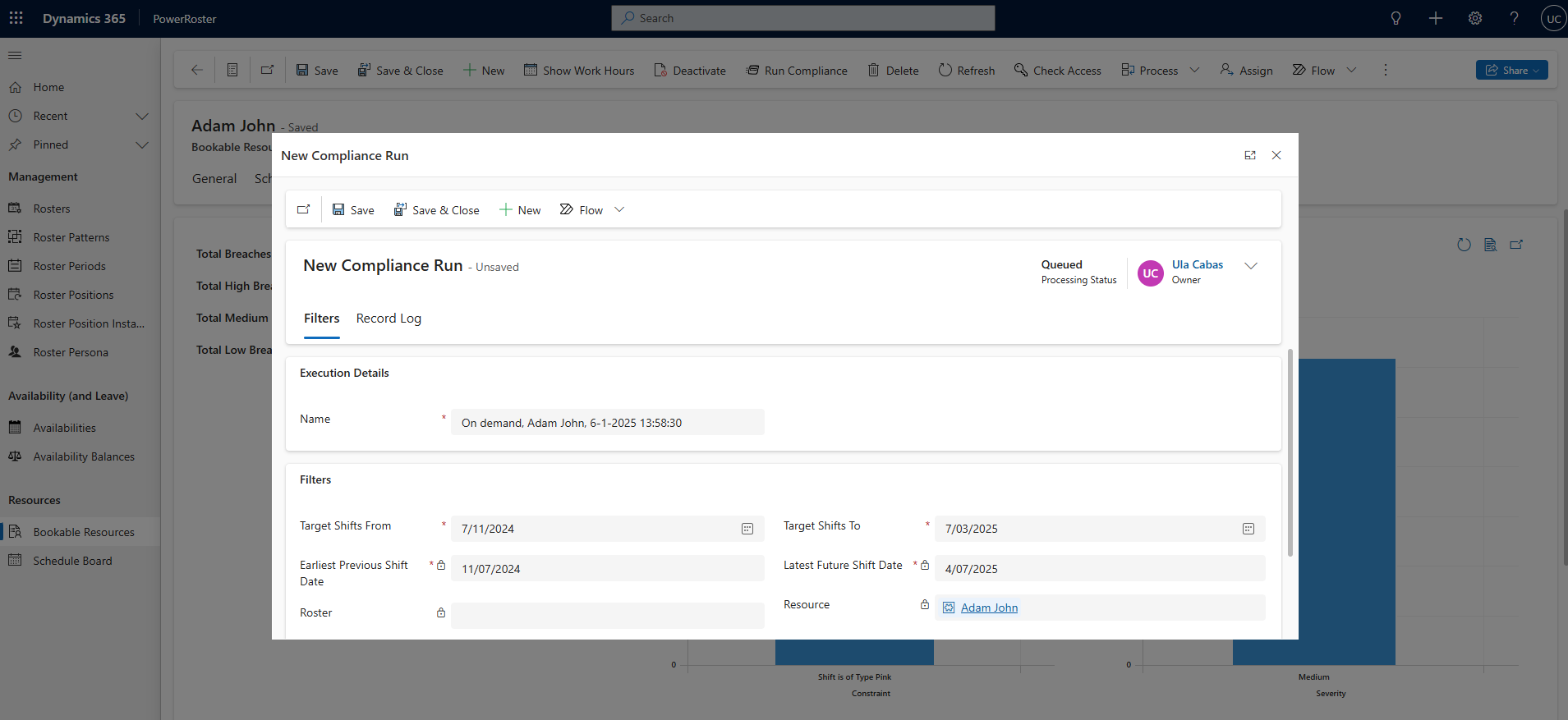
Fill in the required fields for the New Compliance Run and click on Save.
Field
Description
*Name
Auto populated.
*Target Shifts From
Select the start date of the compliance run. Auto calculated but can be changed by the user.
*Target Shifts To
Select the end date of the compliance run. . Auto calculated but can be changed by the user.
*Earliest Previous Shift Date
Auto populated based on the offset values set by the administrator.
*Latest Future Shift Date
Auto populated based on the offset values set by the administrator.
Roster
The Roster against which the Compliance will be run.
Resource
The Resource against which the Compliance will be run.
Compliance Notifications
Once the Compliance Run is saved and complete, this section will show all the compliance breaches linked to that Compliance Run.
How to Run Compliance for a Bookable Resource
To run compliance from the Bookable Resource record:
Navigate to PowerRoster App > Bookable Resources > Open the Bookable Resource record that you want to use for the compliance check.
Select Run Compliance in the Command bar to create a new Compliance Run.
Fill in the required fields as filled above.
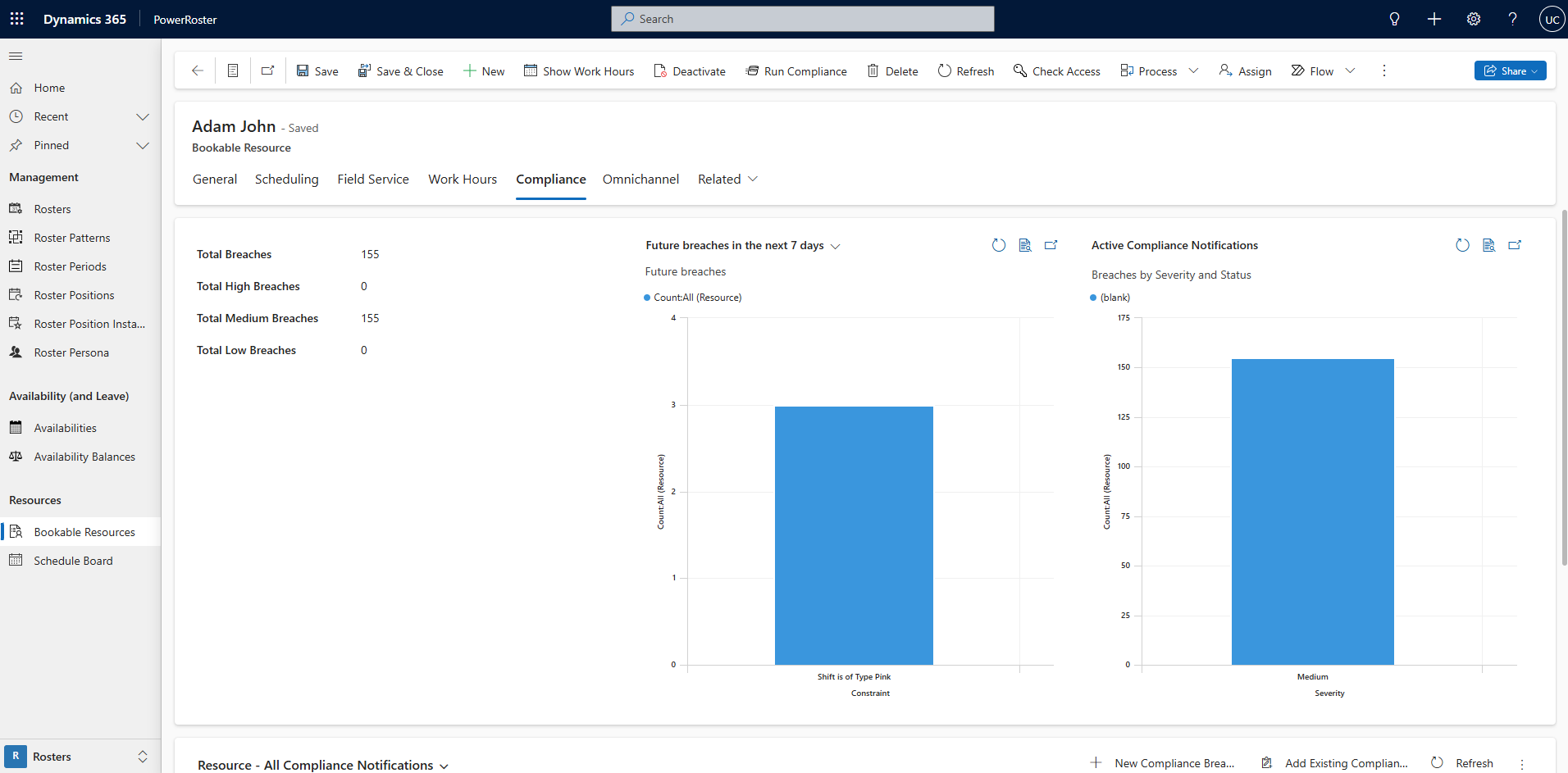
The Compliance tab on the Bookable Resource or the Roster displays compliance data.
Total Breaches are displayed along with a breakdown by the severity of the breaches. The Future breaches chart displays breaches arising in the near future and this data can be filter by date ranges. The Breaches by Severity and Status chart display breaches in a bar chart split by severities and statuses.
Video Walkthrough
The following video demonstrates how to create a Compliance run from a Roster.
Sebastian Brown has been associated with a Roster Position Instance for a Nurse, and since the “Day Shift and Maximum Shift Hours Compliance Contract“ contract has been allocated to Sebastian Brown, the compliance breaches against two incorrect shifts will be displayed once the Compliance Run is Complete.